Power On, Risks Off – Prioritizing the Need for OT Security in the Energy and Utilities
January 31, 2024
While technology continues to advance, it’s important to note that cybersecurity awareness and proactive measures have not kept pace. This observation is particularly evident in operational technology (OT), where the systems responsible for running production plants, controlling power stations, managing water utilities, and overseeing various industrial processes often must be more adequately shielded from cyber threats. Many of these installations are classified as critical infrastructure due to their pivotal role in ensuring safety, sustaining daily life, and bolstering a nation’s economy. In this blog, we delve into the current state of OT security and its importance now more than ever.
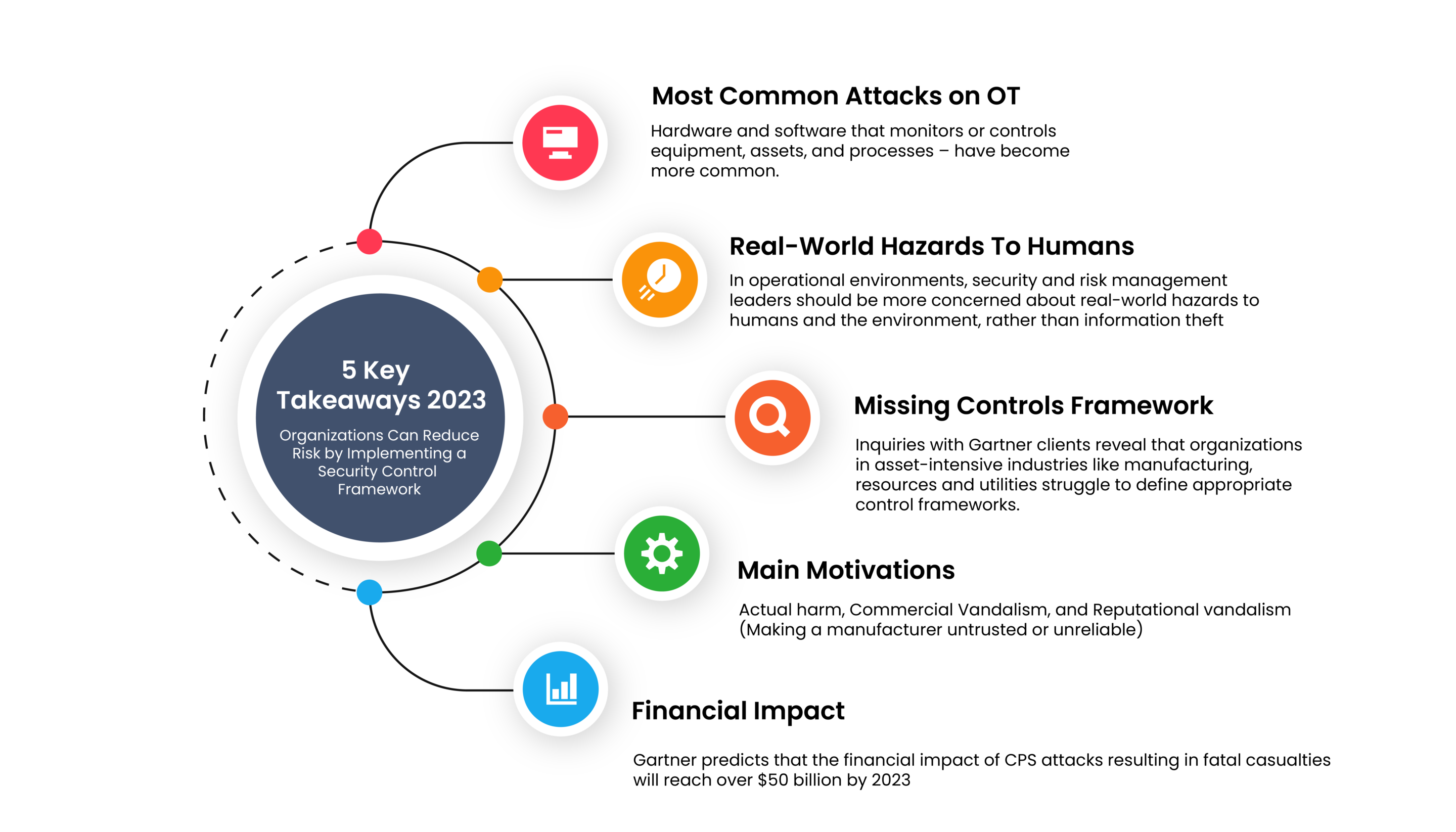
“Gartner predicts by 2025 cyber-attacks will have weaponized operational technology environments to successfully harm or kill humans “
OT (Operational Technology) Security serves as the foundation of a company’s technological infrastructure to ensure a robust and reliable environment for the seamless operation of all business processes. This comprehensive term encompasses hardware, software, and services that empower organizations to efficiently collect, analyze, store, and communicate information in alignment with their business objectives.
In the Energy and Utilities sector, the OT environment faces susceptibility to cyber-attacks due to its extensive network infrastructure, powering critical processes and holding vital data. Recognizing its pivotal role, companies increasingly acknowledge the necessity to safeguard it. The key lies in a personalized security control framework tailored to energy and utility organizations. Components include firewalls for monitoring network traffic, antivirus software as a vigilant guardian, and intrusion detection systems (IDS) for real-time alerts. As the industry strengthens cyber defences, collaboration and innovative solutions become paramount for protecting critical infrastructure and ensuring secure energy resource delivery.
Why OT Security is crucial?
According to Cyber Threat Intelligence, Ransomware Attacks Against The Energy Sector are on the rise – Nuclear, Oil & Gas Are Major Targets In 2024. In the ever-evolving landscape of Energy and Utilities, OT security has begun to gain prominence due to evolving industrial systems and the convergence of digital technologies with critical infrastructure. A few pivotal reasons behind this heightened focus are:
- Increased Vulnerability: Without robust OT security measures in place, the Energy and Utilities sector becomes increasingly vulnerable to cyber threats. The lack of adequate security controls exposes critical infrastructure to potential attacks, such as ransomware, data breaches, and sabotage. These threats can disrupt services, causing economic losses and negatively impacting public safety.
- Legacy Systems: Outdated legacy systems, lacking modern cybersecurity features, pose a significant risk. Many of these systems lack routine security updates and patches, rendering them appealing targets for hackers. The difficulty in upgrading or replacing these systems compounds the challenge of securing Operational Technology (OT) infrastructure.
- Interconnected Networks: The Energy and Utilities sector operates within a complex network of interconnected systems, including both OT and IT environments. This interconnectivity increases the attack surface and creates potential entry points for cybercriminals. A lack of proper segmentation between these networks can allow threats to propagate and compromise critical infrastructure.
- Insider Threats: Malicious or careless employees and contractors with access to OT systems can intentionally or inadvertently cause significant damage. Unauthorized access, weak access controls, and the lack of monitoring and accountability mechanisms contribute to this challenge.
- Limited Investment in Cybersecurity: Traditionally, the focus in the sector has been on prioritizing reliability and availability over investments in cybersecurity. As a result, there is often a lack of dedicated cybersecurity teams, technologies, and protocols specific to the sector. Insufficient investment in cybersecurity hinders the sector’s ability to address OT security challenges effectively.
- Lack of Awareness and Training: Employees and operators may not be adequately educated on the risks, best practices, and potential consequences of cyber threats. This knowledge gap hampers the sector’s ability to proactively mitigate risks and respond effectively to incidents.
Recent Incidents
February 2023: PetroChina Indonesia, a prominent oil and gas regulatory company, allegedly fell prey to a ransomware attack, joining the growing list of critical infrastructures targeted by hackers. The details of the oil and gas company were disclosed on the dark web through a post on the Medusa Blog. The hacker collective responsible for the breach escalated the situation by demanding a ransom for the deletion of the compromised data, extending the deadline, and issuing a threat to sell the information if their demands were not met.
October 2022: Lithuania’s state-owned energy group Ignitis suffered a cyberattack affecting IT systems. The incident demonstrates the vulnerability of national energy grids and the risk of data breaches within the sector.
Securing Critical Infrastructure
Cyber threats in these sectors often target the manipulation, disruption, or unauthorized access to OT systems. Securing Operational Technology (OT) is a paramount concern to ensure the reliability, safety, and resilience of critical infrastructure. Regulations and standards play a crucial role in providing frameworks, guidelines, and benchmarks for organizations to enhance OT security:
- SCADA Systems (Supervisory Control and Data Acquisition)/ Industrial Control Systems (ICS): Crucial for critical infrastructure, SCADA systems monitor and control processes like power generation and water treatment. Cyberattacks on SCADA systems can lead to unauthorized control, causing disruptions or damage. Cyber threats to ICS can impact reliability and safety.
- The North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP): The role of NERC CIP plays a vital role in governing operational technology (OT) security in the energy sector. These mandatory cybersecurity standards are specifically designed to protect the critical infrastructure of the North American electric utility industry, focusing on securing the OT used in the generation, transmission, and distribution of electric power.
Source: https://www.otorio.com/resources/what-is-nerc-cip/
Benefits of Strengthening OT Security Foundations
According to the State of Industrial Security, approximately 90% of manufacturing organizations had their production or energy supply hit by some form of cyberattack. Companies need to invest in appropriate technologies, processes, and skills to protect themselves from external threats while providing secure access to critical information within their internal network and ensuring that risks are appropriately mitigated by the criticality of assets. This includes:
- Securing Critical Infrastructure: Implementing robust authentication mechanisms like multifactor or two-factor authentication via mobile apps or SMSs prevents unauthorized access, safeguarding network resources. OT security defends against cyber threats that could disrupt operations and cause widespread damage.
- Preventing Production Downtime: Cyberattacks on industrial systems can result in production downtime, leading to financial losses and supply chain disruptions. OT security measures play a crucial role in preventing and mitigating the impact of such disruptions.
- Ensuring Safety and Reliability: OT systems control processes with heavy machinery, chemicals, and hazardous materials. Securing these systems is essential for ensuring the safety and reliability of operations, protecting both human lives and the environment.
- Protecting Intellectual Property: Production processes often involve proprietary technologies and trade secrets. OT security safeguards intellectual property by preventing unauthorized access to sensitive information and proprietary processes.
- Compliance with Regulations: Industries, especially critical infrastructure, face strict regulatory requirements for critical infrastructure security. Implementing OT security measures helps organizations comply with regulations, avoiding potential legal consequences.
- Maintaining Operational Continuity: Operational continuity is essential in industries where any disruption can have cascading effects. Recognizing the imperative for elevated security in specific systems, a tailored strategy becomes essential. Implementing robust methods to evaluate the value and criticality of OT assets empowers organizations to prioritize operational continuity, all the while fortifying security measures.
- Risk Management: OT security solutions incorporate real-time technologies for swiftly detecting and responding to cyber threats. This includes conducting risk assessments, implementing security best practices, and staying informed about emerging threats.
- Building Stakeholder Trust: Demonstrating a commitment to OT security enhances stakeholder trust. Organizations prioritizing the security of their operations and data are more likely to engage with customers, investors, and partners.
OT Resilience: Best Practices for Company Posture Assessment
Assessing a company’s Operational Technology (OT) posture involves evaluating the security measures, practices, and resilience of its industrial control systems and critical infrastructure. Here are concise steps to effectively gauge and strengthen the OT posture:
- Perform a focused cybersecurity risk assessment on the OT environment, identifying assets, vulnerabilities, and potential threats impacting system integrity.
- Gain insight into the company’s OT architecture, identifying Industrial Control Systems (ICS), SCADA systems, and critical processes within the OT network.
- Review and Assess network segmentation between IT and OT systems to contain threats and prevent lateral movement within the network.
- Evaluate access controls, ensuring they follow the principle of least privilege for employees, vendors, and stakeholders interacting with OT systems.
- Verify the company’s approach/practices to patch management in the OT environment to reduce the risk of software vulnerabilities.
- Examine incident response and recovery plans specific to OT, evaluating the organization’s readiness to detect, respond, and recover from cyber incidents.
- Review the effectiveness of OT-specific security policies, ensuring employee awareness and compliance with policies relevant to industrial processes.
- Evaluate physical security measures, including access controls, surveillance systems, and measures preventing unauthorized physical access to OT equipment.
- Evaluate security practices of vendors and third-party suppliers with access to the OT environment, assessing risks associated with the supply chain.
- Penetration Testing and Vulnerability Assessments on OT systems to identify and remediate vulnerabilities before malicious exploitation.
- Monitor industry-relevant threat intelligence to stay informed about emerging threats, vulnerabilities, and attack vectors targeting OT environments.
- Collaborate with OT security experts or specialized third-party organizations for valuable insights, assessments, and recommendations to enhance OT security.
- Ensure compliance with relevant regulations and standards governing OT security in the industry, such as NIST SP 800-82 and IEC 62443.
Remember, assessing the OT posture is an ongoing process. Continuous adaptation of cybersecurity measures, regular audits, updates, and employee training are crucial for maintaining a robust OT security posture in the face of evolving threats.
MSSP Services for OT security
As an MSSP, Innova offers a range of specialized services to enhance the cybersecurity posture of critical infrastructure sectors:
- 24/7 Monitoring and Incident Response: We provide continuous monitoring of network activities, coupled with rapid incident response capabilities to swiftly address, and mitigate cyber threats.
- Vulnerability Management: We regularly assess and patch vulnerabilities in systems, ensuring that critical infrastructure remains resilient against emerging threats.
- Compliance Management: We assist organizations in aligning with government regulations and industry standards to meet compliance requirements and enhance overall security.
- Security Awareness Training: We offer customized training programs to educate the employees on cybersecurity best practices, reducing the risk of insider threats.
- Threat Intelligence Services: We provide up-to-date threat intelligence feeds tailored to specific sectors, helping organizations stay ahead of emerging cyber threats.
Secure Your OT now!
The critical importance of OT security is due to the evolving threat landscape, the integration of digital technologies, and the pivotal role of industrial systems. The potential for significant consequences in the face of a cyberattack on OT infrastructure underscores the imperative for organizations across sectors to prioritize and invest in robust security measures.
Adopting a comprehensive strategy that integrates both top-down and bottom-up components for assessing OT cybersecurity enables organizations to promptly pinpoint crucial risks in OT environments and operations. This serves as a pivotal initial step for industrial entities embarking on the path to safeguarding against cyber threats that pose risks to their operations.
Specifically, in the critical infrastructure sector, securing OT systems is crucial for ensuring reliability, safety, and resilience. As these industries progress technologically and interconnect, safeguarding OT from cyber threats becomes increasingly significant for the well-being of operations and the broader community.
References
https://www.gartner.com/en/newsroom/press-releases/2021-07-21-gartner-predicts-by-2025-cyber-attackers-will-have-we
https://www.mckinsey.com/capabilities/risk-and-resilience/our-insights/cybersecurity/how-to-enhance-the-cybersecurity-of-operational-technology-environments

Ashish Saxena
President, Retail, Energy, Manufacturing, Transportation, and Technology (REMTT) SBU
Key Contributors: Raghu Mohan – Senior Director, Industry Solutions, REMTT and Dolly Krithika – Lead, Content/ Research & Sales Enablement