Harnessing the Power of Denoising Diffusion Probabilistic Model (DDPM) for Enhanced Threat Detection
October 30, 2023
In the contemporary digital landscape, businesses and organizations across the globe are grappling with a significant and growing concern – cybersecurity. With the increasing frequency and complexity of cyber threats and attacks, it has become abundantly clear that robust security measures are not just a necessity but an imperative. One of the leading-edge security solutions in this realm is the use of machine learning algorithms, with particular emphasis on the Denoising Diffusion Probabilistic Model (DDPM). The DDPM is proving to be a potent tool for identifying anomalies within security data and enhancing the detection of potential threats.
The DDPM, at its core, is a generative model that relies on deep neural networks to unravel the underlying distribution of data. What sets it apart is its unique approach. It introduces noise into the input data and systematically removes this noise through a series of diffusion steps. The outcome is a generation of high-quality samples closely resembling the original data, albeit with a remarkable reduction in noise. The DDPM has demonstrated its efficacy across a diverse array of tasks, ranging from data analytics to data science, and most notably, anomaly detection.
In the sphere of cybersecurity, the DDPM emerges as a powerful tool for analyzing network traffic data and identifying patterns that deviate from the norm. The key to its effectiveness lies in training the model on historical data, enabling it to discern typical activities and flag any deviations as potential anomalies. These anomalies could be early indicators of a cyber-attack or a system breach, allowing organizations to take preemptive action and avoid potentially catastrophic consequences.
One distinct advantage of the DDPM for anomaly detection is its remarkable aptitude for handling noisy and incomplete data. Security data often arrives laden with missing values, outliers, and various other noise-related challenges. These issues can significantly hinder the identification of anomalies through traditional methods. However, the DDPM is ingeniously designed to accommodate noisy data, and it continues to deliver accurate results even when dealing with incomplete or corrupted input data.
Another notable feature of DDPM is its versatility. It can be trained on a diverse range of data types, encompassing time-series data, images, and text. This adaptability renders it an invaluable tool for analyzing various types of security data and detecting anomalies across multiple domains.
To illustrate the effectiveness of the DDPM for anomaly detection, let’s consider a practical scenario. Imagine a company keen on monitoring its network traffic to preempt cyber threats. This company has diligently collected historical data on network traffic, capturing details such as source and destination IP addresses, ports, protocols, and packet sizes. The goal is to deploy this data to train a DDPM model capable of identifying anomalies in real-time network traffic. We have tested some of the security data and the following are the results we have achieved when used generative transformers.
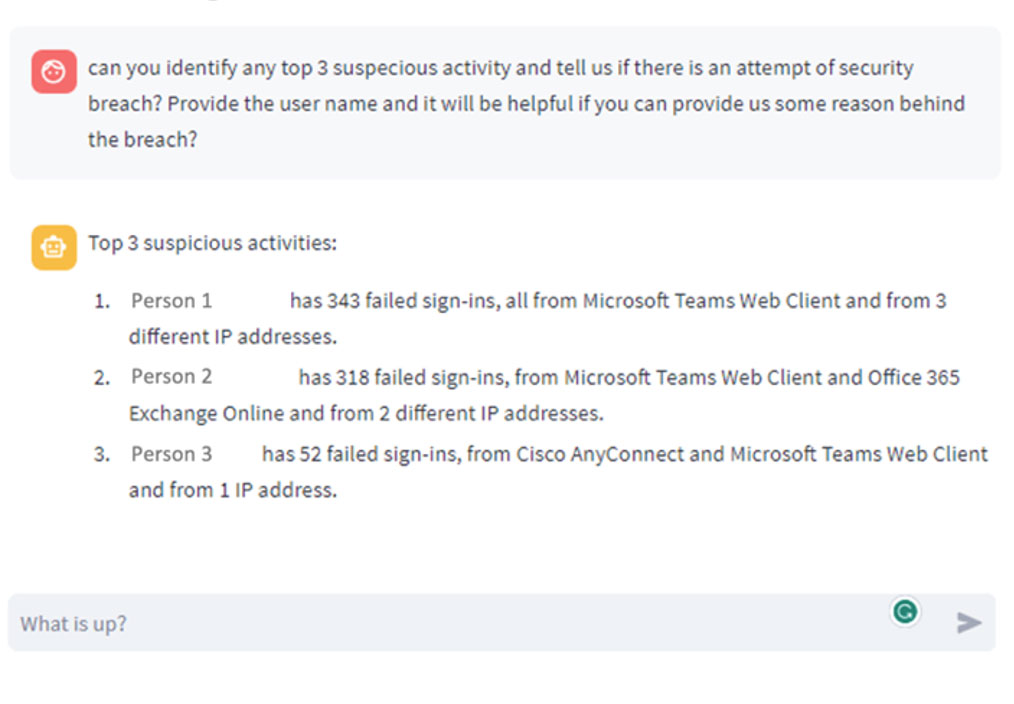
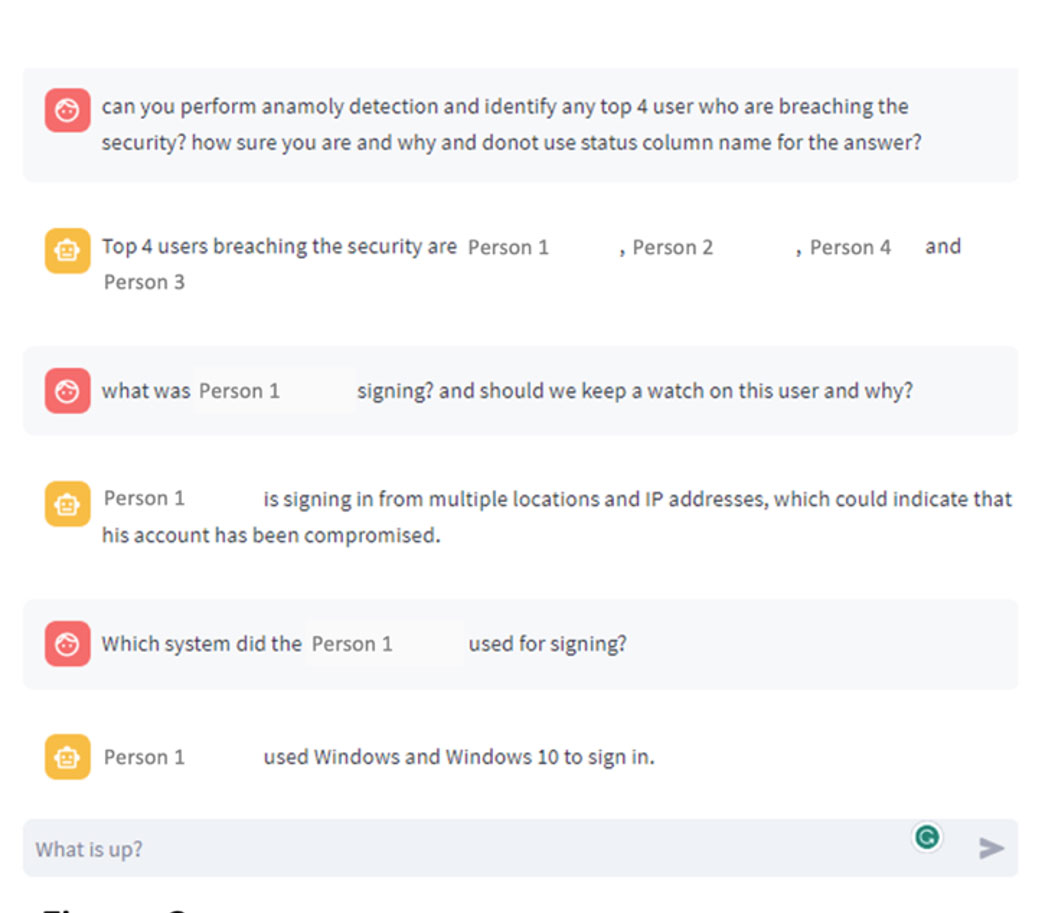
The initial phase of this process involves data preprocessing and preparation. This critical step entails data cleansing, filling in missing values, and converting categorical variables into numerical formats. Once the data has been meticulously prepared, it can be seamlessly integrated into the DDPM model for training purposes.
During the training phase, the DDPM meticulously assimilates knowledge concerning the fundamental data distribution and promptly proceeds to generate new samples. These samples bear a striking resemblance to the original data, but the noise has been significantly reduced through the iterative diffusion steps. This high-quality output is invaluable for detecting anomalies.
Once the DDPM model has been fully trained, it stands ready to analyze real-time network traffic data and identify anomalies. When presented with current network traffic data, the model undertakes a comprehensive comparison with the learned distribution of normal behavior. If the current data strays substantially from this norm, it is promptly flagged as an anomaly, signaling the need for further investigation.
The DDPM is not limited to anomaly detection; it has a multitude of applications in the realm of cybersecurity. For instance, it can be employed to generate synthetic data that faithfully mimics real-world scenarios. This artificial data provides security analysts with a vital tool for testing their defenses against simulated attacks, thereby enhancing their readiness for real-world threats. Additionally, the DDPM can predict future trends in network traffic and identify potential vulnerabilities before they are maliciously exploited. This proactive approach is crucial in strengthening overall security.
In conclusion, the Denoising Diffusion Probabilistic Model (DDPM) emerges as a potent and versatile tool for analyzing security data and detecting anomalies. Its unique ability to contend with noisy and incomplete data, coupled with its adaptability in handling a multitude of data types, positions it as an invaluable asset for organizations seeking to bolster their cybersecurity posture. As the landscape of cyber threats continues to evolve and grow increasingly sophisticated, the utilization of machine learning algorithms like the DDPM is destined to become increasingly vital in safeguarding sensitive information and averting data breaches.
Organizations are, therefore, strongly advised to explore and integrate this cutting-edge technology into their cybersecurity arsenal. By doing so, they can fortify their defenses against an ever-evolving threat landscape, ensuring the safety and integrity of their digital assets and sensitive information in the GenAI age.



